
OB v4 Architecture, cVRP, and VRP+
• by Craig Greenhouse
Part 3 of The Programmable Payments Series
Why Consent Is Now a Policy Object
Open Banking v3 delivered interoperability. Open Banking v4 delivers adversarial security. Variable Recurring Payments deliver programmable delegated financial authority.
This article provides a standards-engineer level architecture deep dive into the security, policy, lifecycle, and core banking enforcement implications of Open Banking v4 and VRP. If you're building financial infrastructure, migrating from v3.x, or trying to understand why VRP requires fundamentally different security primitives, this is for you.
This article assumes familiarity with VRP fundamentals covered in Part 1 and the commercial landscape from Part 2. For a lighter introduction to FAPI 2.0 specifically, see What's New in FAPI 2.0. This piece goes considerably deeper.
Executive Summary
Open Banking v4 and FAPI 2.0 mark a shift from API enablement to adversarial security and policy-driven financial control systems. Variable Recurring Payments require consent to be modelled as enforceable policy objects, tightly coupled to core banking enforcement layers.
For banks and fintechs, OB v4 is not a version upgrade — it is the foundation of programmable finance platforms.
The Architectural Shift: Programmable Financial Operating Systems
Open Banking v4 and Variable Recurring Payments represent the transition from API banking to programmable financial operating systems.
Consent objects become executable policy. Mandates become programmable financial instruments. Policy engines become core banking infrastructure. Banks move from transaction processors to distributed cryptographic control planes enforcing delegated financial authority.
OB v4 and VRP are not incremental Open Banking upgrades. They are the foundation of programmable finance platforms.
1. Open Banking v3.x to v4.x: From PSD2 APIs to Financial-Grade Security Systems
1.1 OB v3.x: The PSD2-Era Security Baseline
Open Banking v3.x was designed in the PSD2 era, when the primary objective was interoperability and market bootstrapping, not adversarial security hardening.
Key characteristics:
- OAuth 2.0 authorization code flow
- Mutual TLS (mTLS) at the transport layer
- Static OAuth scopes for consent representation
- Bearer access tokens
- Directory-issued X.509 certificates for trust bootstrap
Architecturally, OB v3.x treated consent as metadata attached to OAuth scopes, not as an enforceable policy object.
1.2 OB v4.x: Aligning with Financial-Grade API (FAPI)
Open Banking v4.x represents a structural shift from API enablement to adversarial security posture, aligning with:
- FAPI 1.0 Advanced
- FAPI 2.0 security profiles
- OAuth 2.1 baseline
- Rich authorization Requests (RAR)
- Pushed authorization Requests (PAR)
- JWT-Secured authorization Response Mode (JARM)
In OB v4.x, the Open Banking API layer becomes a cryptographically hardened financial control plane with tight coupling to core banking enforcement layers.
1.3 Security Posture Delta: v3.x vs v4.x
| Capability | OB v3.x | OB v4.x |
|---|---|---|
| Token Binding | Sender-constrained (mTLS) | Sender-constrained (mTLS or DPoP) |
| Implicit Flow | Allowed | Forbidden |
| PKCE | Optional | Mandatory |
| PAR | Optional | Mandatory (FAPI 2) |
| JARM | Optional | Mandatory (FAPI 2) |
| RAR | Not used | Mandatory for VRP |
| Consent Representation | OAuth scopes | Structured policy objects |
1.4 Architectural Implication
OB v4.x is not a drop-in API upgrade. It is a distributed cryptographic protocol system with tight coupling to core banking enforcement layers.
TPP App |<------>| AS / OB Gateway |<------>| Core Banking Systems |
| | | | |
| OAuth 2.1 + FAPI | Policy Enforcement |
| PAR / RAR / JARM | Mandate Engine |2. FAPI 2.0: OAuth for Adversarial Financial Systems
2.1 What FAPI 2.0 Actually Changes
FAPI 2.0 is not incremental hardening. It assumes a hostile environment where:
- Browsers are untrusted
- Clients may be compromised
- Networks are adversarial
- Tokens will be stolen unless cryptographically bound
2.2 Mandatory Security Requirements
FAPI 2.0 mandates:
- OAuth 2.1 baseline
- PAR for authorization request integrity
- JARM for authorization response integrity
- Sender-constrained access tokens
- Signed request objects
- Unbound bearer tokens are disallowed in FAPI 2 Advanced; sender-constrained tokens are required (via mTLS or DPoP)
- No implicit flow
- Strict redirect URI matching
This mitigates major OAuth attack classes.
2.3 Sender-Constrained Tokens
Tokens MUST be bound to a cryptographic key:
- Mutual TLS certificate binding - token bound to client certificate
- DPoP (Demonstration of Proof-of-Possession) - token bound to ephemeral key pair
- per-request proof JWT
- nonce replay protection
This prevents:
- Token replay attacks
- Token exfiltration attacks
- Insider API misuse
2.4 Threat Model Shift
| Attack | OAuth 2.0 | FAPI 2.0 |
|---|---|---|
| Code Injection | Possible | Mitigated (JARM) |
| Request Parameter Tampering | Possible | Mitigated (PAR) |
| Token Replay | Possible | Mitigated (sender-constrained) |
| Phishing Redirect Abuse | Common | Strongly mitigated |
3. OAuth 2.1: Removing Two Decades of Legacy Complexity
3.1 OAuth 2.1 as a Consolidation Profile
OAuth 2.1 merges:
- OAuth 2.0 core
- Security Best Current Practices (BCP)
- Implicit flow deprecation
- Mandatory PKCE
- TLS minimum enforcement
3.2 Removed Features
OAuth 2.1 formally removes:
- Implicit flow
- Resource Owner Password Credentials (ROPC) flow
- Token delivery in URL fragments
- Weak redirect patterns
3.3 Architectural Consequences for Banks
Banks must:
- Refactor legacy OAuth authorization servers
- Rebuild SDKs and client libraries
- Refactor mobile and SPA OAuth patterns to use authorization code + PKCE and remove implicit-flow assumptions.
- Harden redirect and token handling logic
OAuth 2.1 is an operationally breaking change for many bank estates still running OAuth 2.0-era assumptions (though spec-wise it is a consolidation profile, not a new protocol).
4. PAR, RAR, and JARM: Hardening the Authorization Channel
Open Banking v4 and FAPI 2.0 fundamentally redesign the OAuth authorization channel. Historically, OAuth treated the browser as a semi-trusted conduit. FAPI assumes the browser is hostile.
4.1 Pushed Authorization Requests (PAR)
4.1.1 Problem Statement
In OAuth 2.0, authorization requests are sent via front-channel redirects:
GET /authorize?client_id=...&scope=...&redirect_uri=...This design is vulnerable to:
- Parameter tampering
- Consent manipulation
- Injection of malicious redirect URIs
- Browser-based interception
4.1.2 PAR Architecture
PAR moves the full authorization request server-to-server:
TPP -> AS (PAR Endpoint) -> returns request_uri
Browser -> AS /authorize?request_uri=...4.1.3 Example PAR Request
POST /par HTTP/1.1
Content-Type: application/jwt
Authorization: Bearer <client_assertion>
{
"iss": "tpp.example",
"aud": "https://bank.example/as",
"response_type": "code",
"client_id": "tpp-client-id",
"redirect_uri": "https://tpp.example/cb",
"scope": "openid payments",
"claims": { ... }
}Note: The above is an illustrative JSON payload within the JWT rather than the JWT itself.
PAR Response
{
"request_uri": "urn:ietf:params:oauth:request_uri:abc123",
"expires_in": 90
}Normative Requirement (FAPI 2):
The Authorization Server MUST support Pushed Authorization Requests.
4.2 Rich Authorization Requests (RAR)
4.2.1 Why Scopes Are Insufficient
OAuth scopes are string labels, incapable of expressing:
- Payment caps
- Merchant allowlists
- Frequency limits
- Time-bound mandates
- Risk policies
VRP requires structured, machine-readable Authorization semantics.
4.2.2 RAR Object Structure
RAR introduces the
authorization_details
object:
"authorization_details": [
{
"type": "urn:openbanking:vrp",
"instructedAmount": {
"amount": "500.00",
"currency": "GBP"
},
"frequency": "Monthly",
"validity": {
"from": "2026-01-01",
"to": "2026-12-31"
},
"merchant": {
"name": "ACME Utilities Ltd",
"merchant_id": "123456"
}
}
]4.2.3 Architectural Implication
RAR turns OAuth from permission tokens into delegated financial authority contracts.
Normative Requirement:
For VRP, Authorization Servers MUST interpret authorization_details as enforceable policy objects.
4.3 JWT-Secured Authorization Response Mode (JARM)
4.3.1 Problem Statement
OAuth authorization responses historically used query parameters:
https://client/cb?code=abc123&state=xyzThis is vulnerable to:
- Code injection
- Mix-up attacks
- Parameter manipulation
- Malicious intermediaries
4.3.2 JARM Architecture
JARM wraps the authorization response in a signed JWT:
HTTP/1.1 302 Found
Location: https://tpp.example/cb?response=<JWT>Note: JARM may be delivered via query, fragment, or form_post mode. In regulated deployments, query or form_post is more typical than fragment.
4.3.3 Example JARM Response JWT Payload
{
"iss": "https://bank.example/as",
"aud": "tpp-client-id",
"code": "abc123",
"state": "xyz",
"exp": 1735689600
}Normative Requirement:
Authorization Servers MUST sign authorization responses using JWS.
4.4 Combined FAPI 2 authorization Flow
TPP Backend Browser AS Policy Engine
| | | |
|-- PAR -------->| | |
|<-- request_uri-| | |
| |-- Redirect ->| |
| | |-- Authenticate User -->|
| | |-- Policy Review UI --->|
| |<-- User Consent -------------------|
| |<-- JARM JWT--| |
|-- Token Request ------------->| |
|<-- Sender-bound Token --------| |
|-- API Call w/ Proof --------->|-- Policy Enforcement ->|
4.5 Security Guarantees Introduced
| Threat | Mitigation |
|---|---|
| Request tampering | PAR |
| Consent manipulation | RAR |
| Code injection | JARM |
| Browser MITM | JARM + PAR |
| Token replay | Sender-constrained tokens |
4.6 Operational Considerations
Banks implementing PAR/RAR/JARM must address:
- Request object storage and expiry
- Policy validation latency
- JWT signing key management (HSM recommended)
- Audit logging of consent payloads
- Regulatory evidence retention
5. Scopes Aren't Enough: Consent as Structured Policy Objects
OAuth scopes were designed for coarse-grained permission signalling in consumer APIs. Variable Recurring Payments and commercial delegated payments require machine-enforceable financial delegation constraints.
5.1 Limitations of OAuth Scopes
Traditional Open Banking consent models used scopes such as:
scope=accounts payments openidScopes suffer from fundamental limitations:
- Flat string semantics
- No parameterisation
- No enforceable constraints
- No linkage to core banking controls
- No lifecycle semantics
Scopes describe what but not how, when, how much, or to whom.
5.2 Consent as a Policy Object
FAPI and OpenID RAR introduce structured consent objects that encode financial delegation constraints. Consent becomes policy-as-data, not metadata.
5.3 VRP Consent Object Example (RAR)
"authorization_details": [
{
"type": "urn:openbanking:vrp",
"mandate": {
"max_amount": {
"amount": "500.00",
"currency": "GBP"
},
"periodicity": "Monthly",
"max_payments_per_period": 10,
"validity": {
"start": "2026-01-01T00:00:00Z",
"end": "2026-12-31T23:59:59Z"
},
"merchant": {
"name": "ACME Utilities Ltd",
"merchant_id": "GB-123456789"
},
"beneficiary_account": {
"iban": "GB29NWBK60161331926819"
}
}
}
]5.4 Normative Enforcement Requirements
Authorization Servers MUST:
- Persist consent policy objects
- Bind policy objects to mandate identifiers
- Enforce constraints at execution time
- Audit all policy decisions
Resource Servers MUST:
- Validate mandate ID
- Validate policy constraints
- Reject transactions violating policy
5.5 Consent Policy Enforcement Architecture
+-------------------+
| Consent Store |
| (Immutable Log) |
+-------------------+
|
v
+-------------------+ +-------------------+
| Policy Engine | ---> | Core Banking |
| (OPA / Custom) | | Payment Engine |
+-------------------+ +-------------------+
^
|
+-------------------+
| OB Gateway / AS |
+-------------------+
5.6 Policy Enforcement Flow (Execution-Time)
TPP -> Payment API -> OB Gateway -> Policy Engine -> Core Banking
|
+--> Reject if policy violated5.7 Consent Object State Machine
Consent is not static. It has lifecycle semantics:
+------------+
| Proposed |
+------------+
|
v
+------------+ Suspend +------------+
| Active | --------------> | Suspended |
+------------+ +------------+
| |
| Revoke | Reactivate
v v
+------------+ +------------+
| Revoked | | Active |
+------------+ +------------+
|
v
+------------+
| Expired |
+------------+
5.8 Consent vs Core Banking Mapping
| Consent Field | Core Banking Control |
|---|---|
| max_amount | Transaction limit engine |
| periodicity | Standing order scheduler |
| merchant_allowlist | Beneficiary validation |
| validity_window | Mandate expiry logic |
| frequency | Velocity monitoring |
| mandate_id | Ledger reference metadata |
5.9 Legal and UX Coupling
Consent UI, legal contract, and enforcement code must be isomorphic:
UI Text <--> Legal Terms <--> Policy Object <--> Enforcement LogicAny divergence introduces regulatory and litigation risk.
5.10 Consent as a Contract
VRP consent is not merely user preference. It is a legally binding delegated authority contract encoded as JSON.
5.11 Storage and Audit Requirements
Banks should:
- Store consent objects in immutable append-only logs
- Hash consent payloads for tamper detection
- Provide regulatory replay capability
- Retain consent evidence for statutory periods
5.12 Performance Considerations
Policy enforcement must occur:
- At authorization
- At execution
- On mandate amendment
- On mandate revocation
Latency budgets must be compatible with real-time payment rails.
6. VRP Mandate Lifecycle Architecture
Variable Recurring Payments introduce long-lived delegated financial authority. This requires a formal mandate lifecycle with explicit state transitions, auditability, and enforcement semantics.
6.1 Mandate Lifecycle Overview
A VRP mandate is a first-class financial object with its own lifecycle, distinct from OAuth tokens:
Consent Object -> Mandate Record -> Execution Policy -> Ledger ReferenceMandates persist longer than OAuth sessions and tokens.
6.2 Mandate State Machine
+-----------+
| Draft |
+-----------+
|
v
+-----------+ Activate +-----------+
| Pending | ----------> | Active |
+-----------+ +-----------+
|
+---------+---------+
| | |
Suspend Revoke Expire
| | |
v v v
+-----------+ +-----------+ +-----------+
| Suspended | | Revoked | | Expired |
+-----------+ +-----------+ +-----------+
|
| Reactivate
v
+-----------+
| Active |
+-----------+
6.3 Mandate Creation Flow
Sequence Diagram
TPP Backend Browser AS OB Gateway Policy Engine Core Banking
| | | | | |
|-- PAR ------------>| | | |
|<-- request_uri ----| | | |
| |-- Redirect --------->| | |
| | |-- Auth UI -->| | |
| | | |<-- Consent Capture --------|
| | |<-- Policy Validate ------->| |
| |<-- JARM JWT ---------| | |
|-- Token Request ----------------->| | |
|<-- Sender-bound Token ------------| | |
|-- Create Mandate API ------------>| | |
| | | |-- Persist Mandate -------->|
|<-- Mandate ID --------------------| | |
6.4 Mandate API (Normative)
Create Mandate
POST /open-banking/vrp/mandates
Authorization: Bearer <sender-bound-token>
Content-Type: application/json
{
"consent_id": "consent-abc123",
"policy": { ...authorization_details... }
}Response
{
"mandate_id": "mandate-xyz789",
"status": "Active",
"created_at": "2026-01-23T12:00:00Z"
}6.5 Mandate Execution Flow
Execution is decoupled from consent:
TPP -> Payment Execution API -> Policy Check -> Core Banking -> SettlementExecution Request
POST /open-banking/vrp/payments
{
"mandate_id": "mandate-xyz789",
"amount": {
"amount": "45.00",
"currency": "GBP"
},
"reference": "Invoice 12345"
}6.6 Execution-Time Policy Enforcement
Policy Engine must validate:
| Constraint | Enforcement |
|---|---|
| max_amount | Per-transaction limit |
| max_payments_per_period | Velocity rules |
| periodicity | Scheduling constraints |
| merchant_allowlist | Beneficiary whitelisting |
| account_scope | Account-level entitlement |
Normative requirement:
The Payments Engine MUST reject execution if any limit rule fails.
6.7 Mandate Amendment
Mandates are mutable but require user re-authorization:
TPP -> PAR/RAR Amendment -> User Auth -> Policy Update -> Mandate Version++Mandates should be versioned immutably.
6.8 Mandate Suspension and Reactivation
Suspend Mandate
POST /mandates/{mandate_id}/suspendReactivate Mandate
POST /mandates/{mandate_id}/reactivateSuspension must prevent execution but retain policy and audit history.
6.9 Mandate Revocation
Revocation permanently invalidates the mandate:
DELETE /mandates/{mandate_id}Normative requirement:
Resource Servers MUST reject any execution referencing a revoked mandate.
6.10 Mandate Expiry
Mandates must auto-expire when:
- Validity end date reached
- Account closed
- Regulatory revocation event occurs
6.11 Idempotency Requirements
Payment execution must support idempotency keys:
Idempotency-Key: 550e8400-e29b-41d4-a716-446655440000Banks must guarantee exactly-once execution semantics.
6.12 Audit and Evidence Requirements
Banks must log:
- Mandate creation
- Amendments
- Execution events
- Policy violations
- Revocation events
Logs should be immutable and cryptographically hashed.
6.13 Mandate vs Token Lifetimes
| Object | Typical Lifetime |
|---|---|
| Access Token | Minutes/Hours |
| Refresh Token | Days/Months |
| VRP Mandate | Months/Years |
Mandates become long-lived delegated financial instruments.
7. Mapping Consent and Mandates to Core Banking Enforcement
Open Banking consent objects and VRP mandates are meaningless unless enforced by core banking systems. This section describes the architectural coupling required between Open Banking gateways and internal banking domains.
7.1 Core Banking Enforcement Domains
A VRP execution request intersects multiple internal banking domains:
| Domain | Function |
|---|---|
| Limits Engine | Transaction and velocity constraints |
| Payments Engine | Execution and routing |
| AML/Fraud Engine | Risk scoring and screening |
| Ledger / GL | Financial posting and reconciliation |
| Customer Profile | Account state and eligibility |
| Treasury | Liquidity and funding management |
7.2 High-Level Enforcement Architecture
+-------------------+ +-------------------+
| OB Gateway / AS | ---> | Policy Engine |
+-------------------+ +-------------------+
|
v
+-------------------+
| Payments Engine |
+-------------------+
|
+-----------------------+-----------------------+
| | |
v v v
+-------------------+ +-------------------+ +-------------------+
| Limits Engine | | AML / Fraud | | Ledger / GL |
+-------------------+ +-------------------+ +-------------------+7.3 Execution-Time Enforcement Flow
TPP -> OB API -> Policy Engine -> Payments Engine
| |
v v
Limits Check AML/Fraud Scoring
| |
+-------+----------+
|
v
Ledger Posting7.4 Limits and Velocity Controls
Mandate constraints must map to internal limit controls:
| Consent Constraint | Limits Engine Mapping |
|---|---|
| max_amount | Per-transaction limit |
| max_payments_per_period | Velocity rules |
| periodicity | Scheduling constraints |
| merchant_allowlist | Beneficiary whitelisting |
| validity_window | Mandate expiry logic |
These constraints must be enforced consistently across all execution paths.
7.5 Payments Posting Model
7.5.1 Internal Posting Flow
Customer Account (DR) -> VRP Clearing Account (CR)
VRP Clearing Account -> Beneficiary Settlement (DR)Banks should maintain a VRP suspense/clearing account for reconciliation and dispute handling.
Banks may implement intermediate nostro or payments hub accounts depending on rail architecture.
7.5.2 Ledger Metadata Propagation
Mandate metadata must be propagated into the General Ledger:
{
"mandate_id": "mandate-xyz789",
"consent_id": "consent-abc123",
"tpp_id": "tpp-client-id",
"policy_hash": "sha256:deadbeef...",
"execution_reference": "Invoice 12345"
}This metadata is critical for:
- Regulatory audit
- Dispute resolution
- Revenue attribution
- Fraud analytics
7.6 AML and Fraud Integration
VRP execution must trigger AML and fraud pipelines:
7.6.1 Screening
- Sanctions list checks
- Beneficiary screening
- Velocity anomaly detection
7.6.2 Risk Scoring Inputs
Risk models should ingest:
- Mandate age
- TPP reputation
- Merchant category
- Historical execution patterns
- User behavioural biometrics
7.7 Real-Time Fraud Controls
Policy engines should expose dynamic risk gates:
If risk_score > threshold:
suspend mandate
require step-up authenticationVRP mandates introduce long-lived fraud surfaces, unlike one-off payments.
7.8 Treasury and Liquidity Impacts
VRP introduces predictable but binding cash flow commitments.
Treasury systems should:
- Forecast mandate-based outflows
- Allocate liquidity buffers
- Stress-test mandate concentration risk
Large-scale VRP adoption materially affects intraday liquidity management.
7.9 Reconciliation Architecture
7.9.1 Settlement Reconciliation
Banks must reconcile:
- Mandate execution logs
- Payment rail settlement reports
- Internal ledger postings
7.9.2 Reconciliation Keys
| Key | Source |
|---|---|
| mandate_id | Consent system |
| payment_id | Payments engine |
| settlement_id | Clearing rail |
| ledger_entry_id | GL system |
7.10 Dispute and Chargeback Handling
Unlike card chargebacks, VRP disputes require:
- Mandate evidence replay
- Policy compliance proof
- Customer consent artefacts
Banks must maintain cryptographic consent evidence to defend disputes.
7.11 Revenue and Cost Attribution
Banks should attribute:
- VRP execution fees
- TPP charges
- Internal processing costs
Metadata tagging enables product P&L measurement.
7.12 Operational Resilience Requirements
VRP enforcement systems must meet:
- Tier-1 availability SLAs
- Real-time latency budgets
- Active-active deployment
- Regulatory operational resilience frameworks (e.g., UK FCA)
OB gateways become systemically important financial infrastructure.
8. Dual-Stack Migration Patterns: Running OB v3 and OB v4 in Parallel
No tier-1 bank will perform a flag-day migration from OB v3.x to OB v4.x. Regulatory obligations, third-party dependencies, and internal core banking constraints require dual-stack coexistence for years.
8.1 Brownfield Reality Constraints
Banks migrating to OB v4 must contend with:
- Legacy OAuth 2.0 authorization servers
- v3.x TPP contractual obligations
- Legacy SDKs embedded in fintech applications
- Core banking systems with hard-coded assumptions
- Regulatory continuity requirements
OB v4 must be introduced without breaking existing TPP integrations.
8.2 Dual-Stack Architecture Overview
TPPs (v3) -------> | OB v3 API Gateway |
+-------------------+
|
v
+-------------------+
| Core Banking |
| Systems |
+-------------------+
^
|
TPPs (v4) -------> | OB v4 API Gateway |
+-------------------+Key principle: OB v3 and OB v4 must be logically isolated at the API and security layers, but may converge at the core banking enforcement layer.
8.3 API Version Routing Strategies
8.3.1 Path-Based Versioning
/open-banking/v3.1/...
/open-banking/v4.0/...Advantages:
- Explicit version negotiation
- Simplest TPP integration
- Regulatory clarity
8.3.2 Hostname-Based Segregation
api-v3.bank.example
api-v4.bank.exampleAdvantages:
- Complete blast-radius isolation
- Independent TLS and certificate stacks
8.3.3 Gateway Policy Routing
If client supports FAPI2:
route -> v4 stack
Else:
route -> v3 stackThis requires dynamic metadata discovery and client capability negotiation.
8.4 Security Stack Segregation
OB v3 and OB v4 must not share security components:
| Layer | v3 Stack | v4 Stack |
|---|---|---|
| OAuth Server | Legacy OAuth 2.0 | OAuth 2.1 + FAPI 2 |
| Token Format | Bearer | Sender-constrained |
| Consent Model | Scopes | Policy Objects (RAR) |
| Auth Response | Query Params | JARM JWT |
| PAR | Optional | Mandatory |
8.5 Contract Translation Layer (Compatibility Shim)
Banks may introduce a contract translation layer to bridge v3 and v4:
TPP v3 Request -> Translation Layer -> v4 Internal Policy ModelExample Translation
// v3 Scope Model
"scope": "payments"
// Translated to:
"authorization_details": [
{ "type": "urn:openbanking:legacy:payments" }
]This approach should be treated as temporary technical debt, not a permanent solution.
8.6 Blue/Green Deployment for OB v4
OB v4 should be deployed using blue/green or canary patterns:
OB v4 Blue Stack <----> Load Balancer
OB v4 Green Stack <----> Load BalancerThis is critical due to:
- Cryptographic dependencies
- HSM integration
- Regulatory incident reporting requirements
8.7 TPP Migration Incentivisation
Banks should:
- Provide sandbox and conformance tooling
- Offer commercial incentives for v4 adoption
- Publish migration timelines with regulatory consultation
Forced migrations without tooling will fail.
8.8 Backwards Compatibility Risks
8.8.1 Token Semantics Drift
Bearer tokens in v3 vs sender-bound tokens in v4 create non-trivial developer friction.
8.8.2 Consent Semantics Drift
Scopes vs policy objects create UX and legal contract divergence.
8.8.3 Operational Complexity
Dual-stack doubles:
- Incident response surface
- Monitoring complexity
- Security patching burden
8.9 Core Banking Convergence Layer
Despite API dual-stack, core banking should converge to a single enforcement layer:
OB v3 Gateway -> Policy Adapter -> Core Policy Engine
OB v4 Gateway -> Policy Adapter -> Core Policy EngineThis reduces duplicated business logic.
8.10 Data Model Harmonisation
Banks must harmonise:
- Consent data models
- Mandate identifiers
- Ledger metadata schemas
Failure to harmonise results in irreconcilable regulatory reporting divergence.
8.11 Decommissioning Strategy
Banks should publish a staged decommissioning roadmap:
- Freeze new v3 integrations
- Incentivise v4 adoption
- Mandate v4 for VRP and high-risk products
- Sunset v3 with regulatory approval
8.12 Regulatory and Governance Considerations
Dual-stack operation must be approved by:
- Internal risk committees
- Regulators (e.g., FCA, CMA, CBPR)
- Third-party risk governance
OB v4 becomes systemically important infrastructure and falls under operational resilience frameworks.
9. Threat Models Unique to VRP and Delegated Payment Mandates
Variable Recurring Payments introduce persistent delegated financial authority, creating attack surfaces that don't exist in single-payment APIs. This section enumerates adversarial threat models and required mitigations.
9.1 Threat Model Overview
VRP systems must assume:
- Malicious TPPs
- Compromised client applications
- Phished or coerced users
- Insider threats
- Network and protocol-level adversaries
- Malware on customer devices
VRP mandates represent standing attack primitives - a successful compromise yields ongoing extraction capability.
9.2 Mandate Hijacking Attacks
Attack Vector
An attacker gains control of a mandate identifier and attempts to execute payments.
Methods
- API token exfiltration
- Mandate ID enumeration
- Insider misuse
- Logging system compromise
Mitigations
| Control | Description |
|---|---|
| Sender-constrained tokens | Prevent token replay |
| Mandate binding to TPP ID | Enforce client identity |
| Non-guessable mandate IDs | UUIDv4 or equivalent entropy |
| Execution context validation | Check TPP, account, and policy binding |
9.3 Consent Phishing and Social Engineering
Attack Vector
User is tricked into approving a malicious mandate (e.g., disguised merchant, deceptive UI, inflated limits).
Attack Scenarios
- Fake utility companies
- Dark patterns in consent UI
- Consent fatigue exploitation
- QR-code initiated mandate traps
Mitigations
- Mandatory merchant verification
- Consent UI summarisation with risk signals
- Cooling-off periods for high-risk mandates
- User revocation dashboards
Normative guidance:
Authorization Servers SHOULD implement behavioural and UX safeguards against consent coercion.
9.4 Policy Downgrade Attacks
Attack Vector
TPP attempts to reduce policy constraints after mandate creation (e.g., increase max amount, expand merchant scope).
Mitigations
- Mandate version immutability
- Mandatory user re-authentication for policy change
- Signed mandate policy hashes
9.5 Mandate ID Enumeration and Replay
Attack Vector
Sequential or predictable mandate identifiers enable brute-force execution attempts.
Mitigations
- High-entropy mandate identifiers
- Rate-limiting execution endpoints
- Execution-time policy validation
- Mandatory idempotency keys
9.6 Insider Threats
Attack Vector
Bank employees or compromised internal services manipulate mandates or bypass policy enforcement.
Mitigations
- Segregation of duties
- Immutable audit logs
- Dual-control administrative actions
- Privileged access monitoring
9.7 Compromised TPP Applications
Attack Vector
TPP backend compromised, leading to mass mandate abuse.
Mitigations
- TPP behavioural monitoring
- Mandate execution anomaly detection
- Transaction velocity limits per TPP
- Real-time revocation capability
9.8 Policy Engine Bypass
Attack Vector
Execution routed around policy engine via legacy payment channels.
Mitigations
- Network segmentation
- Mandatory policy enforcement hooks in payments engine
- Policy decision logs enforced at gateway and core layers
9.9 Replay and Idempotency Abuse
Attack Vector
Replaying execution requests to trigger duplicate payments.
Mitigations
- Idempotency keys
- Payment intent identifiers
- Exactly-once execution semantics
9.10 Mandate Lifecycle Race Conditions
Attack Vector
Simultaneous revocation and execution causing inconsistent enforcement.
Mitigations
- Strong consistency guarantees
- Revocation-before-execution checks
- Distributed locking or consensus mechanisms
9.11 Merchant Spoofing and Beneficiary Substitution
Attack Vector
TPP swaps beneficiary account while preserving merchant branding.
Mitigations
- Beneficiary cryptographic binding to mandate
- Merchant registry validation
- Signed beneficiary identity assertions
9.12 Long-Lived Mandate Risk Accumulation
Mandates accumulate risk over time:
- Changes in customer circumstances
- Dormant mandates forgotten
- TPP ownership changes
- Regulatory changes
Mitigations
- Periodic mandate revalidation
- Mandatory expiry dates
- Customer reminders and dashboards
9.13 Attack Tree Summary
Goal: Extract Funds via VRP
|
+-- Phish Consent
| +-- Fake Merchant UI
| +-- Dark Pattern Consent
|
+-- Steal Mandate ID
| +-- Token Exfiltration
| +-- Enumeration
|
+-- Bypass Policy Engine
| +-- Legacy Payment Path
| +-- Insider Override
|
+-- Replay Execution
+-- Duplicate Requests
+-- Race Conditions9.14 Normative Security Controls Summary
Banks MUST implement:
- Sender-constrained tokens
- PAR, RAR, JARM
- Mandate policy binding
- Immutable audit logs
- Idempotent execution APIs
- Merchant and beneficiary verification
Banks SHOULD implement:
- Behavioural analytics
- Consent UX safeguards
- Periodic mandate revalidation
- Real-time mandate kill switches
10. Federation, Policy Engines, and the Bank-as-Platform Future
Open Banking v4 and VRP are not the end state. They are transitional architectures toward federated financial trust frameworks and programmable banking platforms.
This section provides a brief overview. A dedicated future article will explore these topics in depth, including OpenID Federation, policy-as-code engines (OPA/Cedar), event streaming architectures, and the evolution toward bank-as-platform models.
10.1 OpenID Federation and Trust Frameworks
Current Open Banking ecosystems rely on:
- Central directories
- Static X.509 trust anchors
- Manual onboarding workflows
These models do not scale globally or across multi-jurisdiction ecosystems.
OpenID Federation introduces:
- Entity Statements
- Trust Marks
- Federation Hierarchies
- Machine-verifiable trust metadata
This enables dynamic, cryptographically verifiable ecosystem trust. Future VRP systems will operate across federated trust domains.
10.2 Policy Engines as Financial Control Planes
Legacy banks embed policy in:
- COBOL
- Java payment engines
- Manual configuration
Modern architectures externalise policy into policy engines such as Open Policy Agent (OPA), Cedar (the policy language used by AWS Verified Permissions), or Rego-based systems.
Example policy (Rego-style):
allow_payment {
input.amount <= data.mandate.max_amount
input.merchant == data.mandate.merchant_id
time.now >= data.mandate.validity.start
time.now <= data.mandate.validity.end
}Policies become versioned, auditable, testable, and deployable.
10.3 Bank as a Programmable Financial Platform
VRP, policy engines, and federation enable Bank-as-a-Platform:
- Programmable mandates
- Conditional payments
- Event-driven financial workflows
- Smart escrow and treasury automation
- Embedded finance primitives
Banks expose financial control planes, not just APIs.
10.4 Competitive Implications
Entities that control:
- Policy engines
- Federation trust layers
- Mandate UX
...will control the future financial platform layer.
Traditional banks risk becoming regulated execution utilities.
10.5 Architectural End-State Vision
+-------------------------------+
| Federated Trust Framework |
+-------------------------------+
|
v
+-------------------------------+
| Policy Engine Control |
+-------------------------------+
|
v
+-------------------------------+
| Programmable Payments Core |
+-------------------------------+
|
v
+-------------------------------+
| Treasury, Risk, AI Systems |
+-------------------------------+Open Banking v4 is Phase 1 of Bank-as-Platform.
A future article will explore federation, policy-as-code, event streaming, AI-driven treasury, and platform governance in detail.
Programmable Banking Control Plane Architecture (C4 Container View)
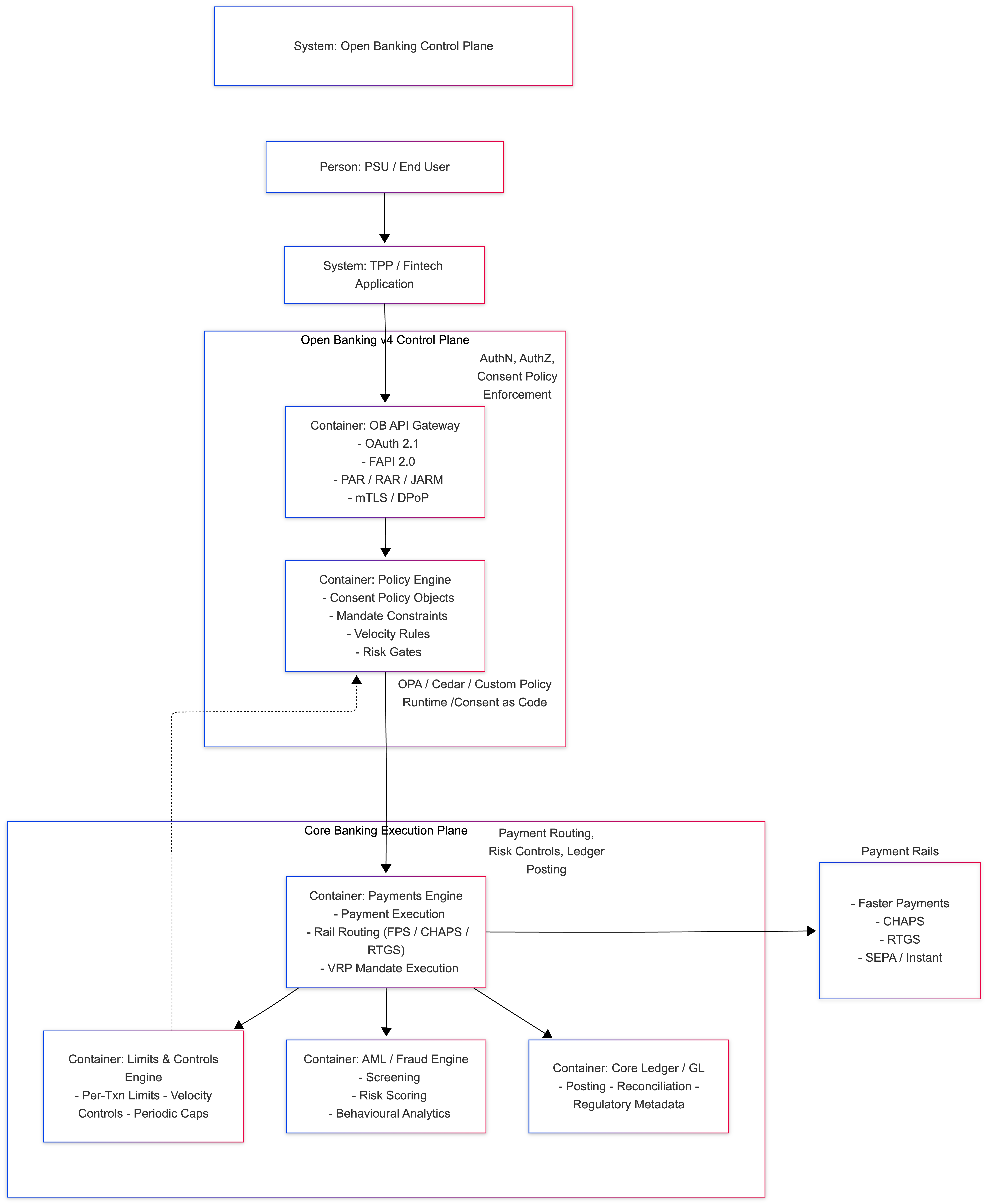
This architecture reframes Open Banking v4 as a control plane and core banking as an execution plane, with VRP mandates acting as programmable financial processes enforced between the two.
CTO / Architect Takeaways
- OB v4 is a cryptographic control plane, not just an API upgrade.
- Consent objects become legally binding policy contracts enforced in core banking systems.
- Dual-stack OB v3/v4 estates will coexist for a decade or more; migration is organisational, not just technical.
- Policy engines (OPA/Cedar) will become core banking infrastructure components.
- Banks that externalise policy and build programmable mandate platforms will become financial platforms; others will be regulated execution utilities.
Conclusion: Open Banking as a Distributed Financial Operating System
Open Banking v3 delivered interoperability.
Open Banking v4 delivers adversarial security.
VRP delivers programmable financial authority.
The next decade will see banks transition from transaction processors to financial platforms. Those who build policy engines, federation frameworks, and programmable mandate systems will define the future of finance. Those who do not will become regulated execution utilities.
OB v4 is not a regulatory upgrade. It is the foundation of distributed programmable finance.
VRP mandates are delegated financial authority encoded as policy objects, enforced by cryptographic primitives, and executed through hardened distributed systems.
Banks that build federation, policy engines, and programmable mandate systems will define the future of finance. Those that do not will become regulated execution utilities.
